Overview of the partition structure.
As well as any other system NTFS divides all useful place into clusters - data blocks used at a time. NTFS supports almost all sizes of clusters - from 512 bytes up to 64 KBytes. The 4 KBytes cluster is considered to be some standard. NTFS doesn't have any anomalies of cluster structure and I have nothing to say about it.
NTFS disk is symbolically divided into two parts. The first 12% of the disk are assigned to so-called MFT area - the space which MFT metafile grows into. Any data recording into this area is impossible. The MFT area is always kept empty not to let the most important service file (MFT) be fragmented at growth. The rest 88% of the disks represent usual space for files storage.
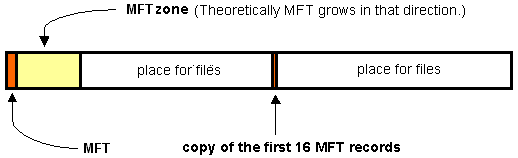
MFT and its structure
MFT is divided into records of the fixed size (usually 1 KBytes), and each record corresponds to some file. The first 16 files are housekeeping and they are inaccessible to the operating system. They are named metafiles and the very first metafile is MFT itself. These first 16 elements MFT are the only part of the disk having the fixed position. It is interesting that the second copy of the first 3 records, for reliability (they are very important) is stored exactly in the middle of the disk. The remaining MFT-file can be stored as well as any other file at any places of the disk. It is possible to re-establish its position with its own help using the basis - the first MFT element.
Metafiles
The first 16 NTFS files (metafiles) are system files. Each of them is responsible for some aspect of system operation. The advantage of such modular approach is in amazing flexibility - for example on FAT the physical failure in the FAT area is fatal for all disk operation. As for NTFS it can displace and even fragment on the disk all system areas avoiding any damage of the surface except the first 16 MFT elements.
The metafiles are in the NTFS disk root directory, they start with a name character "$", though it is difficult to get any information about them by standard means. Curiously that even for these files the quite real size is reported, and it is possible to find out for example how many operating system spends on cataloguing of all your disk having looked at $MFT file size. In the following table the metafiles used at the moment and their function are indicated.
| $MFT | Itself MFT |
| $MFTmirr | copy of the first 16 MFT records placed in themiddle of the disk |
| $LogFile | journaling support file (see below) |
| $Volume | housekeeping information - volume label, file system version, etc. |
| $AttrDef | list of standard files attributes on the volume |
| $. | root directory |
| $Bitmap | volume free space bitmap |
| $Boot | boot sector (bootable partition) |
| $Quota | file where the users rights on disk space usage arerecorded (began to work only in NT5) |
| $Upcase | File - the table of accordance between capital andsmall letters in files names on current volume. It isnecessary because in NTFS file names are stored inUnicode that makes 65 thousand various characters and itis not easy to search for their large and smallequivalents. |
- Last modification time: For directories, this is the last time an entry was added, renamed, or removed. For other file types, it's the last time the file was written to.
- Last access (read) time: For directories, this is the last time it was searched. For other file types, it's the last time the file was read.
- Last status change: Examples of status changes are change of owner, change of access permission, change of hard link count, or an explicit change of any of the MAC times.
- Deletion time: ext2 and ext3 record the time a file was deleted in the
dtimetimestamp, but not all tools support it. - Creation time: ext4fs records the time the file was created in the
crtimetimestamp, but not all tools support it.
The different timestamps are stored in the metadata contained in the inodes. Inodes are similar to the MFT entry number in the Windows world. One way to read the file metadata on a Linux system is to first
get the inode number using the command
ls -i file
then use
istat against the partition device and specify the inode number. This will show you the different metadata attributes, including the timestamps, the file size, owner's group and user id, permissions, and the blocks that contain the actual data.
Comments
Post a Comment